Designing and Deploying Access Control Systems: Best Practices and Principles
It is a typical Friday morning. Walter arrives at his former workplace after being dismissed a week earlier. He is angry and out for revenge. As he walks to the door, he pulls his access card from his wallet to gain entry. What are the odds that the card was removed from the access program, and he is now unable to enter the building?
The situation is not unique, nor is it a scenario that is difficult to resolve. Security deployments must consider the protection of people, property and physical assets, and access control is the first line of defense. Managing access to these resources requires designing and deploying a system guided by the best strategic practices and principles.
Involve Stakeholders
Access control has many features and capabilities, including multiple authentication features, video surveillance authentication and numerous locking hardware assemblies. Because security is not a code-driven effort, end-user/stakeholder involvement is essential throughout the project's life cycle to bridge needs with an acceptable plan of action and for an integrator to address those needs during installation.
In many cases, this effort will need coordination with other trades like electrical, lighting, low voltage telecommunications, and fire and life safety as it relates to egress in emergency events. It also relies on collaboration with the end user to understand the sequence of operations for all deployed access control systems. For example, tiered access control, where one card might access one area but another might have an entirely different access capability, must be determined during the programming of systems.
Because it is the security designer’s role to take the design from concept to final installation and commissioning, it is also their responsibility to champion stakeholders’ involvement, ensuring their voices are heard in the design and deployment of the access control system. Designers must ensure the quality of installation and adherence to the design as indicated in the design package and respond to requests for information and changes. They must also participate in scheduled progress meetings to ensure the project is proceeding on time and there are no delays due to lack of response.
Review Designs at the Conceptual Level
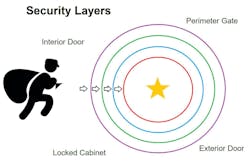
When developing a security strategy for access control, it’s important to start at the conceptual level with the fundamental principle of Security-in-Depth (SID), also known as Concentric Circles of Protection or Concentric Rings of Security. Similar to strategies employed by military planners, SID is the method of using layered and complementary security controls to deter, detect, delay and deny unauthorized intrusions. Whether you’re dealing with external bad actors or potential insider threats, each layer offers the opportunity to identify and intercept any attacker who tries to get through.
Throughout each layer, access control is integrated with other systems and key components to prevent intruders from reaching their targets. Systems must be designed to consider the environment on several levels, as well as the floor and site plans. Surveillance and intrusion must also be considered in the deployment of security access systems, along with aligning those components with telecommunications network infrastructure.
Reviewing conceptual site and floor plans in the early stages of design allows for a thorough security evaluation and feedback that benefits all parties. Designers can virtually walk the plans to determine weak points and reduce or remove doors, hallways and overall floor layouts that create unnecessary access control deployment increases and costs. Involving security consultants early in the conceptual design can also help to integrate any changes in the floor plan or use of space and provide logical placement of deployed security resources.
Partner with Quality Manufacturers for the Best Access Control System
Once the basis of design is determined, it is often helpful to involve a security consultant who can assist in identifying an access control system that best meets the organization's needs. Security consultants can leverage their knowledge of emerging technologies and relationships with manufacturers to find a feature-rich, user-friendly system that is easy to train on and designed for longevity of use. Longevity of use is identified through reserve studies and future-proofing infrastructure to allow for flexibility and scalability as time progresses.
When selecting a high-quality manufacturer to partner with, it is essential to scrutinize them beyond the features of the deployed devices, taking into account warranty considerations, lead time for replacement parts and overall support as an active partner. This helps to ensure maximum utilization of features and the training of new staff for long-term deployment.
Establish Standards for Access Control Deployment and Implementation
Establishing an access control standard is the first step in providing the parameters of use and determining how and when access to specific locations can be granted or denied. Defining how users can access the organization's data and systems allows for design and implementation that covers the needs at hand but also considers future security requirements.
On the operational side, documenting the access control system’s design and specifications helps develop standards for future deployments. Documented specifications not only establish performance parameters but also advise future integrators of the client’s installation requirements and provide the necessary training for the operation team. The organization/owner will need to retain all the necessary warranty and licensing information and detailed shop drawings to demonstrate future issues to newly assigned integrators not involved in the original deployment.
Make Access Control a Priority
Ensuring the physical security of the business and protecting employees and assets should be a top priority for any company. These strategic processes establish a firm ground for deploying and maintaining systems for long-term use. Taking a strategic approach and insisting on a collaborative effort from stakeholders from the outset will help provide a solid foundation for any integrated security system.
About the Author
Matthew Harper
Matthew Harper is a Senior Technology Consultant at Jensen Hughes with over 30 years of experience in all aspects of the construction project cycle. A registered communication distribution designer (RCDD), Matthew has worked as an inspector, estimator, project manager, and designer on industrial, commercial, and residential deployments of low-voltage systems with full integration and intuitive control applications for clients around the world.