Electronic Security Technology ≠ A Secure Facility
It seems so easy when you watch CSI. That show has taught us that installing electronic security technologies is a phenomenally effective way to be safe and solve crimes. The lure of inexpensive, reliable, high-quality, and low-maintenance security technology is almost irresistible. If only security programming were that simple.
Building owners, facilities managers, and security professionals are constantly challenged to find security solutions that are operationally and cost effective. All too often, however, the solutions revolve around the use of electronic security technologies without regard to an adequate understanding of organizational assets and the threats, risks, and vulnerabilities that may impact them.
Certainly, electronic security technologies – including secure network video, access control, revolving doors and barrier turnstiles, emergency call stations, and others – are important components of modern security programs; however, it’s essential to recognize that these technologies don’t make a facility secure.
In fact, effective security is a complex “system” requiring an appropriate balance of technologies that are properly designed and installed, effectively managed and maintained, and consistently operated in accordance with organizational requirements; well-written, properly implemented policies, procedures, and processes; training for an engaged facility staff; and professional program management. Absent the proper balance of these elements, the “security system” can’t be successful.
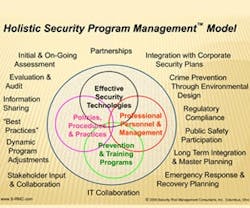
In a broader context, security programming requires a multifaceted effort to be most effective. As illustrated in the model on this page, each of the four core elements (security technology, policies and practices, staff training and engagement, and program management) interacts with every other element to create a flexible, resilient foundation. This foundation, however, should be considered only the beginning.
Individuals responsible for security program management must constantly be aware of changes in their organizational assets along with the dynamic threat paradigm related to the assets. Initial and ongoing assessments are essential. Other key activities include:
- The application of Crime Prevention through Environmental Design (CPTED) concepts and principles.
- The identification and, where appropriate, adoption of the best practices of like facilities.
- Effective stakeholder input and collaboration.
- The development of inter- and intra-organizational partnerships.
- Regulatory compliance (fire/security/lighting/other).
- IT collaboration and planning.
- Coordination with first responders.
- Integration with the facility’s technology/capital master plan.
- The application of information received from fusion centers, law enforcement, and other reliable sources.
After each of these elements is in place, one final series of actions is required: evaluation, testing, audit, and, of course, program adjustment.
Electronic physical security technologies and IT platforms are converging at light speed. This process will create many challenges, along with opportunities to integrate security with building automation systems in support of green buildings and LEED certification. Well-written, properly implemented technology standards are essential; however, key to this effort is ensuring that the chosen technologies are selected based on an assessment of needs, appropriate for the application, organizationally sustainable, properly installed and managed, and, most importantly, part of an integrated, holistic security program.
Elliot A. Boxerbaum is president of Security Risk Management Consultants Inc.. He may be reached at [email protected] or (614) 224-3100.